Security Standpoint . Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. The goal of it security is to protect. Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. What does a cybersecurity risk assessment entail? The 7 layers of cybersecurity. A cybersecurity risk assessment requires an organization to determine its. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. The 7 layers of cybersecurity should center on the mission critical assets you are seeking to. I defined tech ethics as protecting users from harm where we can.
from www.youtube.com
The goal of it security is to protect. A cybersecurity risk assessment requires an organization to determine its. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. The 7 layers of cybersecurity. Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. I defined tech ethics as protecting users from harm where we can. The 7 layers of cybersecurity should center on the mission critical assets you are seeking to. What does a cybersecurity risk assessment entail? Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information.
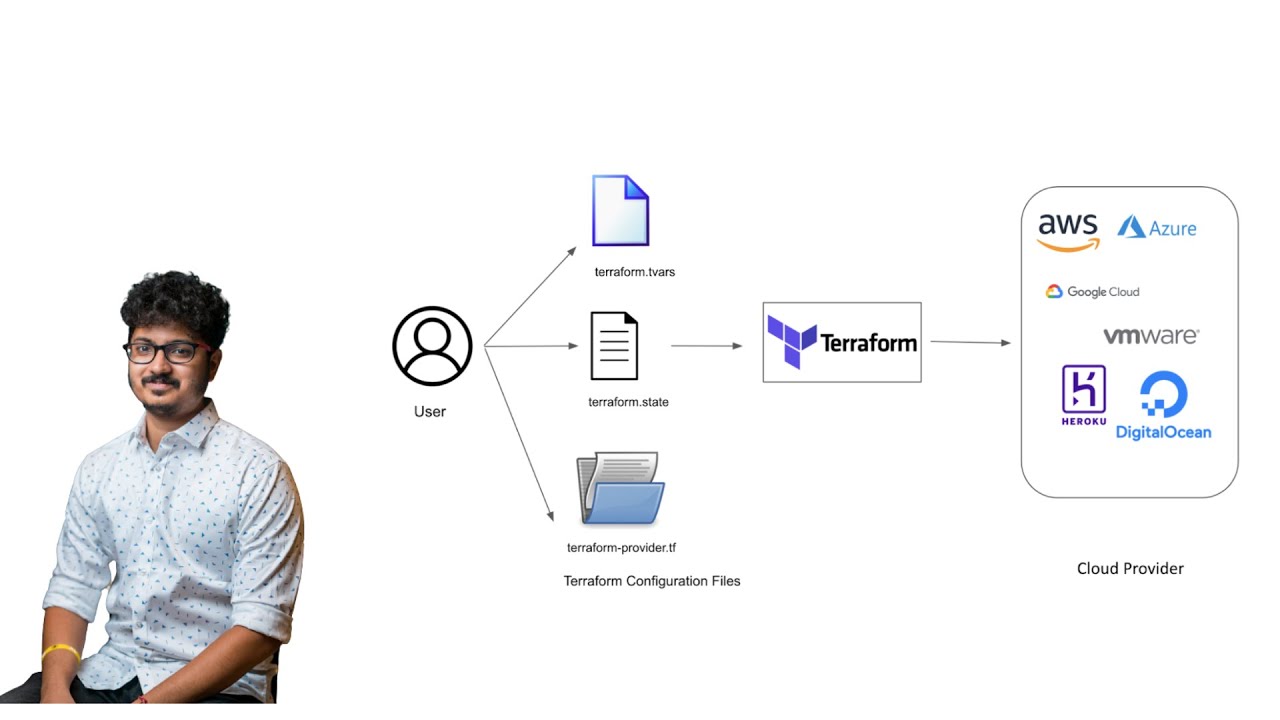
Scenario 18 Repeatable way to Create Infrastructure with Security
Security Standpoint Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. The 7 layers of cybersecurity should center on the mission critical assets you are seeking to. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. A cybersecurity risk assessment requires an organization to determine its. The 7 layers of cybersecurity. The goal of it security is to protect. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. I defined tech ethics as protecting users from harm where we can. What does a cybersecurity risk assessment entail? Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information.
From www.tandfonline.com
Security challenges and policy initiatives an analysis from CPEC Security Standpoint I defined tech ethics as protecting users from harm where we can. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. The 7 layers of cybersecurity should center on the mission critical assets you are seeking to. Similarly, the main aim of security is to try to protect users from people who want to hurt. Security Standpoint.
From www.youtube.com
Let a VISO Show Due Diligence from a Security Standpoint YouTube Security Standpoint What does a cybersecurity risk assessment entail? From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. The goal of it security is to protect. The 7 layers of cybersecurity. Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. I defined tech ethics as. Security Standpoint.
From filmfreeway.com
Standpoint FilmFreeway Security Standpoint The 7 layers of cybersecurity should center on the mission critical assets you are seeking to. What does a cybersecurity risk assessment entail? The 7 layers of cybersecurity. I defined tech ethics as protecting users from harm where we can. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. The. Security Standpoint.
From stormagic.com
StorMagic Enters Security Market with Encryption Key Management Security Standpoint I defined tech ethics as protecting users from harm where we can. Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. What does a cybersecurity risk assessment entail? From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. A cybersecurity risk assessment requires. Security Standpoint.
From www.aisd.net
4,000+ new security cameras installed Bond Security Standpoint Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. The 7 layers of cybersecurity should center on the mission critical assets you are seeking to. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. The 7 layers of cybersecurity. What does a. Security Standpoint.
From www.commercialintegrator.com
Your Lack of Cybersecurity Diligence Is Costing You Business Security Standpoint A cybersecurity risk assessment requires an organization to determine its. The 7 layers of cybersecurity. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. The goal of it security is to protect. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. The 7 layers of. Security Standpoint.
From www.youtube.com
Scenario 18 Repeatable way to Create Infrastructure with Security Security Standpoint The 7 layers of cybersecurity. The 7 layers of cybersecurity should center on the mission critical assets you are seeking to. I defined tech ethics as protecting users from harm where we can. The goal of it security is to protect. What does a cybersecurity risk assessment entail? Similarly, the main aim of security is to try to protect users. Security Standpoint.
From www.craiyon.com
Information security concept on Craiyon Security Standpoint I defined tech ethics as protecting users from harm where we can. The goal of it security is to protect. Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. Infosec, or information security, is a set of tools and practices that you can use to protect your digital. Security Standpoint.
From www.youtube.com
Standpoint YouTube Security Standpoint The 7 layers of cybersecurity. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. What. Security Standpoint.
From www.craiyon.com
Web security concept Security Standpoint The goal of it security is to protect. Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. The 7 layers of cybersecurity. What does a cybersecurity risk assessment entail? Infosec, or information security, is a set of tools and practices that you can use to protect your digital. Security Standpoint.
From thedigitalhacks.com
VPN Remain safe while browsing the web! TDH Online Agency Security Standpoint The goal of it security is to protect. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. What does a cybersecurity risk assessment entail? The 7 layers of cybersecurity. Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. Security for information technology. Security Standpoint.
From pii-tools.com
The Complete Guide to PII PII Tools Security Standpoint I defined tech ethics as protecting users from harm where we can. Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. A cybersecurity risk assessment requires an organization to determine its. The goal. Security Standpoint.
From www.dandssecurity.net
Security Camera System Burbank, Anaheim, Long Beach, Los Angeles, City Security Standpoint What does a cybersecurity risk assessment entail? I defined tech ethics as protecting users from harm where we can. The 7 layers of cybersecurity should center on the mission critical assets you are seeking to. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. From an operational standpoint, this requirement. Security Standpoint.
From biztechnologysolutions.com
How to Properly Onboard/Offboard Employees from a Security Standpoint Security Standpoint The goal of it security is to protect. Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. A cybersecurity risk assessment requires an organization to determine its. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. Similarly,. Security Standpoint.
From independent-connections.com
Why IT Security May Be WellPrepared for the Future Independent Security Standpoint Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. The 7 layers of cybersecurity. What does a cybersecurity risk assessment entail? From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. The goal of it security is to protect. I defined tech ethics as protecting users. Security Standpoint.
From slideplayer.com
Wireless Security. ppt download Security Standpoint Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. What does a cybersecurity risk assessment entail? Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. Security for information technology (it) refers to the methods, tools. Security Standpoint.
From cyshield.com
Cyshield Security Standpoint From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. A cybersecurity risk assessment requires an organization to determine its. Similarly, the main aim of security is to try to protect users from people who want to hurt or rob them. The 7 layers of cybersecurity should center on the mission critical assets you are seeking. Security Standpoint.
From resiliencepost.com
An uneventful G7 from a security standpoint The Resilience Post Security Standpoint I defined tech ethics as protecting users from harm where we can. Infosec, or information security, is a set of tools and practices that you can use to protect your digital and analog information. From an operational standpoint, this requirement refers to adequate response time and/or guaranteed bandwidth. Similarly, the main aim of security is to try to protect users. Security Standpoint.